DdoS Protection
MEfficient, early-stage DDoS mitigation - built into your ADC
SKUDONET protects your infrastructure with scalable, intelligent DDoS mitigation — blocking malicious traffic at the earliest stage of the packet flow. Using early-stage Layer 4 filtering, dynamic policy scaling, and real-time automation, it ensures.



Why Choose SKUDONET for DDoS Protection?
Early-stage packet filtering
L4 filtering is applied where it’s most efficient — before the system’s core resources are affected, reducing CPU and memory exhaustion during high-load events.
Smart analysis at Layer 7
Block abusive patterns and application-level threats like HTTP floods, malformed requests, and excessive bot activity — without degrading legitimate traffic.
Early-stage packet filtering
L4 filtering is applied where it’s most efficient — before the system’s core resources are affected, reducing CPU and memory exhaustion during high-load events.
Real-time visibility
Monitor traffic live, define rate limits, filter by IP, country, or behavior — and respond immediately to threats with granular control rules.
Automated rule response
Define custom rules by traffic type, thresholds, or source behavior – and let SKUDONET apply mitigation policies automatically, without manual intervention.
Dynamic policy scaling
During sustained attacks, SKUDONET
automatically adjusts mitigation rules and response thresholds, prioritizing legitimate traffic and avoiding overblocking.
DDOS FILTERING
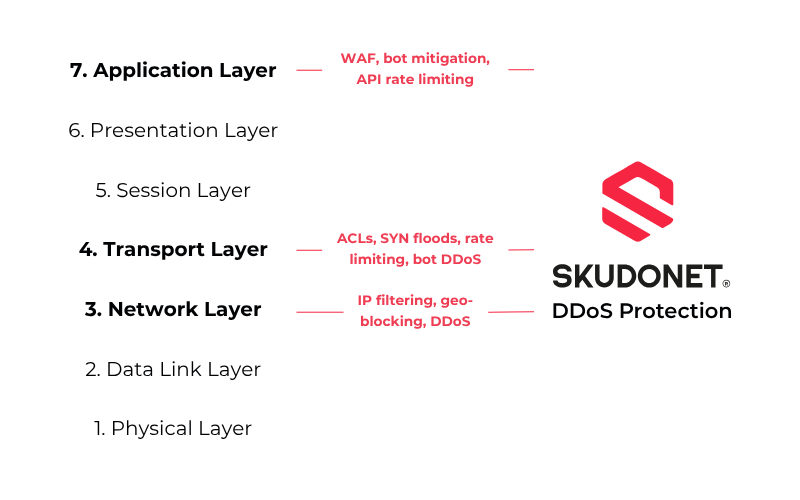
Where and How SKUDONET Stops Attacks
Not all DDos protection is equal. Some tools react once the system is already overwhelmed. SKUDONET stops threats at the edge — applying filters as soon as the traffic reaches the network layer, and enforcing smart rules at the application level. This layered approach combines speed with accuracy.
USES CASES
Common DDoS Scenarios and How SKUDONET Responds
SKUDONET is built to handle both brute-force volumetric attacks and more subtle application-level abuse. Here’s how it responds in real-world scenarios:
SYN/UDP Floods
Dropped at Layer 4 before reaching application logic. Adaptive thresholds minimize false positives.
HTTP/HTTPS Floods
Blocked via Layer 7 rate limiting, anomaly detection, and bot filtering.
Multi-vector attacks
Combined filtering rules mitigate volumetric, protocol, and application abuse simultaneously.
IoT botnet attacks
Detected via IP reputation feeds and blocked at connection level.
Evolving attack patterns
Filtered with heuristic and adaptive rules that learn from abnormal traffic behavior — enabling real-time response even to previously unseen threats.
Want to know how to protect your APPs?
Download our free guide to understand key risks and how SKUDONET defends your critical endpoints.
load balancer solutions
Choose the SKUDONET Deployment That Fits Your Infrastructure
Virtual Load Balancer
Seamlessly integrate SKUDONET into your virtual environment with pre-installed, ready-to-use templates.
Baremetal Load Balancer
Install SKUDONET on your existing hardware for maximum performance and flexibility.
Hardware Load Balancer
Get a robust solution, with SKUDONET ADC pre-installed on dedicated hardware.
Cloud Load Balancer
Run SkudoCloud — a SaaS load balancer with built-in security and no infrastructure to manage.
Learn more about Enterprise Load Balancing Products
CONTACT US
Need More Information?
Write us if you want to know more about our ADC Load Balancer Solution, our technical support team will advise you on everything you need.

