Web Application FIREWALL (WAF)
Advanced Layer-7 Protection for Secure Application Delivery
A full inspection WAF built on ModSecurity and OWASP CRS v4.3.0, designed for engineers who need transparent rule control, predictable performance and deep protocol validation.





SKUDONET WAF
A Fully Automated Security Engine Built for Critical Environments
Rule Transparency & Full Control
- View all OWASP + SKUDONET rules (700+)
- Modify, override, or tune them
- Visual diff between factory rules and custom rules
- Rule-change notifications and update management
High-Availability, Zero-Maintenance
- Full replication of WAF/IPDS configuration
- No exceptions, no manual sync
- Instant failover with consistent policies
Automation & Limitless Scalability
- REST API for CI/CD, dynamic lists, orchestration
- Automatic rule & blocklist updates
- No limits on rules, services, domains
- Performance determined only by system resources
How SKUDONET WAF Processes and Secures Every Request
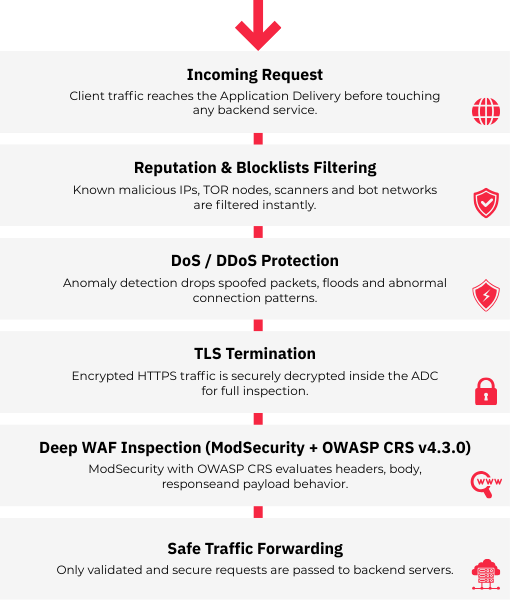
1. Traffic Entry & Pre-Filtering
Incoming requests are checked against automated reputation lists, RBLs and anomaly-based DoS/DDoS detection. Malformed packets, bots, scanners, TOR nodes and spoofed traffic are filtered before deeper inspection.
2. TLS Termination & Protocol Validation
The Application Delivery securely terminates TLS, enabling full encrypted-traffic inspection. SKUDONET validates HTTP methods, header integrity and protocol standards to discard abnormal or tampered requests early.
3. Deep WAF Inspection
Requests are analyzed at body and payload level: SQLi, XSS, RCE, injections, JSON/XML anomalies, file uploads and other advanced threats are detected using a four-phase engine integrated into the Application Delivery Platform.
4. Secure Forwarding & Response Validation
Approved requests are sent to backend servers. Outbound headers and response content are inspected again to prevent leakage, reflected payloads and backend-generated threats before returning data to the client.
Independent Benchmark Results
All results below come from independent evaluations using GoTestWAF, ensuring objective and reproducible metrics.
Advanced Features
High-Performance Protection for Your Web Applications
DoS and DDoS attack mitigation
Specific engine to mitigate denial-of-service attacks, with configurable rules per service: connections per second limit, connections per IP, protection against TCP spoofing, etc.
Integrated IPDS system
Includes intrusion prevention and detection system (IPS/IDS) with blacklists and whitelists, protection against known attacks, and real-time response mechanisms.
Automated blocklists
Over 200 automated reputation lists by zone or geolocation to block suspicious private networks, botnets, spam, TOR nodes, anonymous proxies, scrapers, among others.
Bot detection and mitigation
Identifies and blocks malicious traffic generated by bots, preventing web scraping, credential stuffing, and other automated attacks without affecting legitimate users.
HTTP header validation
Verification of incoming HTTP headers to ensure compliance with protocol standards and mitigate attacks that abuse malformed headers. Also prevents attacks such as header spoofing (e.g., X-Forwarded-For).
Automatic threat response
Real-time blocking of malicious traffic, without the need for manual intervention, thanks to integration with dynamic blacklists and immediate response policies.
Comprehensive protection against advanced threats
Over 400 predefined rules—including OWASP—to detect and block attacks such as SQL injection (SQLi), Cross-Site Scripting (XSS), file inclusion, remote code execution, session fixation, and filtering by unauthorized methods and protocols.
Full scalability and automation
Integration via REST+JSON API to manage the WAF programmatically in dynamic and high-performance environments. Supports over 140,000 simultaneous users at layer 7 and over 10 million at layer 4, with optimized performance up to 40 Gbps.
load balancer solutions
Choose the SKUDONET Deployment That Fits Your Infrastructure
Virtual Load Balancer
Seamlessly integrate SKUDONET into your virtual environment with pre-installed, ready-to-use templates.
Baremetal Load Balancer
Install SKUDONET on your existing hardware for maximum performance and flexibility.
Hardware Load Balancer
Get a robust solution, with SKUDONET ADC pre-installed on dedicated hardware.
Cloud Load Balancer
Run SkudoCloud — a SaaS load balancer with built-in security and no infrastructure to manage.
Learn more about Enterprise Load Balancing Products
related resources
CONTACT US
Need More Information?
Write us if you want to know more about our ADC Load Balancer Solution, our technical support team will advise you on everything you need.

