Contents
- 1 What is Blackboard?
- 2 Blackboard high available environment
- 3 Blackboard load balancing configuration
- 4 Blackboard Load Balancer Cluster
- 5 Blackboard Virtual Services Enhanced Security
What is Blackboard?
Blackboard is an education sector application developed by a company with the same name, whose goal is to serve educative content edited by teachers and easily accessible for students.
This application contains important tools for students like exam tools, video conferences with teachers or course lessons. As this kind of applications expects an elevated number of concurrent users, issues due to application server overload could face everyday.
In order to mitigate it, it’s highly recommended to deploy the web application using a high availability model to guarantee that students can access simultaneously to the educative resources without having connectivity issues and serving the application always with the maximum availability.
Blackboard high available environment
Blackboard environment contains two kinds of servers:
Application servers that manage the application logic and user profiles.
Collaborative servers that are used by some tools as a meeting point between users or chat features. In fact, this is an application server with some special configurations.
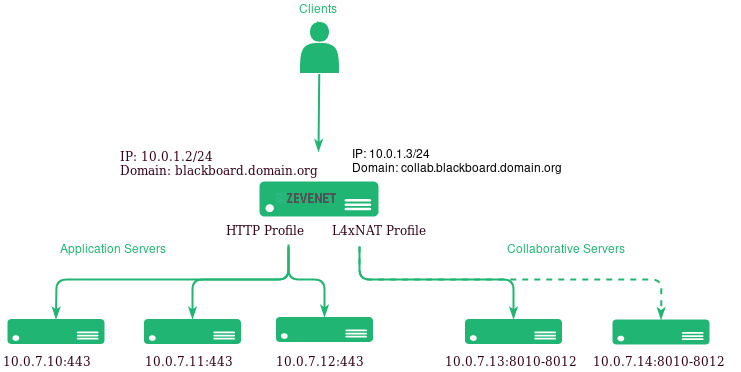
The target scalable and highly available environment of a Blackboard deployment is shown in the draw below.
In order to achieve it, we recommend to setup one HTTP farm for application servers in active-active mode where a pool of servers is added on demand.
On the other hand, we recommend a L4xNAT farm for collaborative servers using all ports and all protocols, as they can use TCP and UDP traffic for the interactive and collaboration services. According to Blackboard, those services only can be setup in active-passive mode so we’ll take it into account during the configuration of the virtual service.
In our example, the Blackboard application service is being published on the IP 10.0.1.2 which resolves for the domain blackboard.domain.org in the DNS and using the TCP ports 443 and 80 (redirecting to the port 443).
The collaborative services are accessible through the IP 10.0.1.3 which resolves with the domain collab.blackboard.domain.org from all ports and protocols.
All the applications and collaborative servers are in the same network segment 10.0.7.0/24.
Blackboard load balancing configuration
Requirements
Firstly, prepare the application to be setup in high availability and some load balancer utils.
Blackboard configuration for high availability
The application and collaborative Blackboard servers configuration for high availability are explained with details in the following article:
Please, follow the instructions of DNS and other configurations required in order to ensure that the Blackboard deployment is ready for HA.
Blackboard virtual service network configuration
The virtual services will be published in two different virtual interfaces under the same physical NIC, those interfaces will be shared between the Zevenet Load Balancer cluster. In cases of high throughput and in order to reduce latency, the virtual services could use different physical NICs.
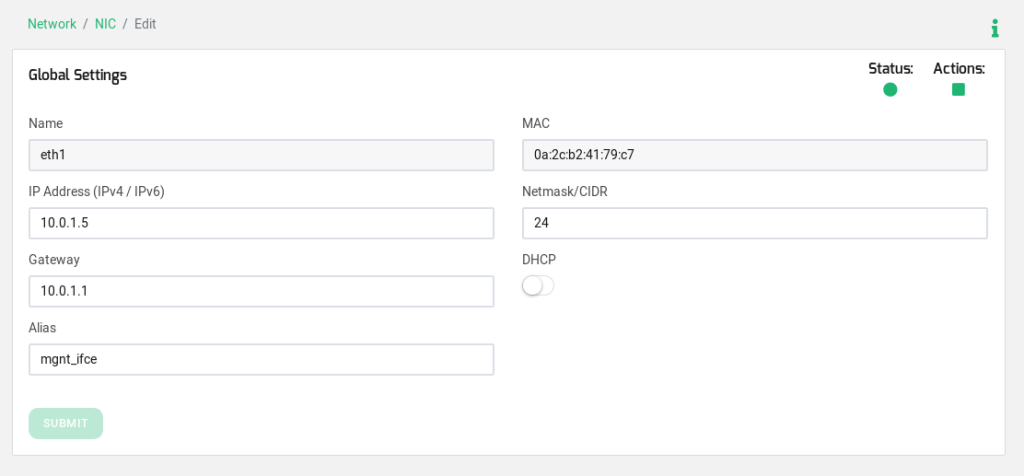
The virtual interfaces are created in an existing physical network interface, so it is necessary to have a NIC, bonding or VLAN interface in the same network than the virtual interface IP address. In this case, one NIC interface is created, clicking on the left menu Network > NIC and editing one of the NICs of the list.
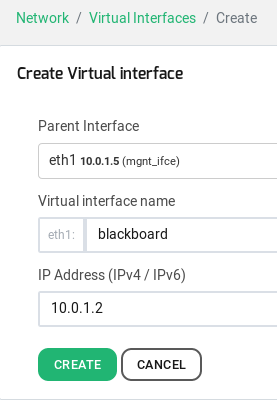
In this example, the services will be published in two interfaces, one called eth1:blackboard using the IP 10.0.1.2 and another called eth1:collab and using the IP 10.0.1.3.
To create a virtual interface click on the left menu bar option Network > Virtual Interfaces > Create and fill up the form like it’s shown below.
In the same way, create the virtual interface for the collaborative virtual service.
Blackboard health check monitoring
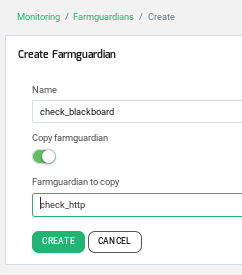
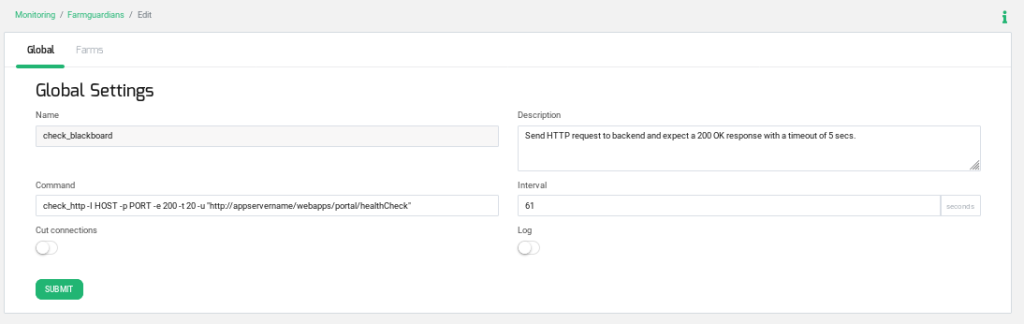
Blackboard already provides a webpage dedicated to asking for the health status of the application server, so we recommend to use it in the advanced health checks configured in the load balancer. The following customized FarmGuardian check will be used to know the Blackboard application status.
Clicking on the left menu bar option Monitoring > Farmguardians, press on Create Farmguardian and choose the option Copy from “check_http”, as it’s shown below.
The new health check parameters for the Blackboard application servers are:
Name: check_blackboard
Interval: 61 seg
Command: check_http -I HOST -p PORT -e 200 -t 20 -u “http://blackboard.domain.org/webapps/portal/healthCheck”
This Farmguardian check is adjusted for 4 backends or less, if there are more than 4 backends in the application servers pool set the interval parameter according to the equation interval=*20+1.
Now that we configured the required setup, let’s go to configure the virtual services for every service needed in Blackboard HA.
Blackboard Application Servers virtual service configuration
Two different HTTP virtual services will be configured, one for secure HTTPS and another one with a redirect from HTTP to HTTPS. Let’s see how to achieve that.
Application Server HTTPS virtual service
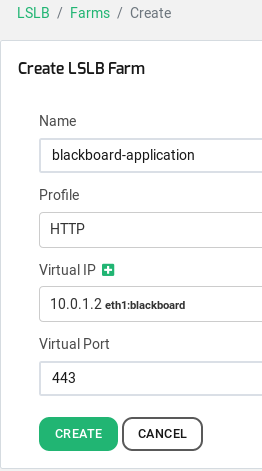
Create a new LSLB HTTP profile farm by clicking on the left menu bar option LSLB > Farms and then the button Create Farm.
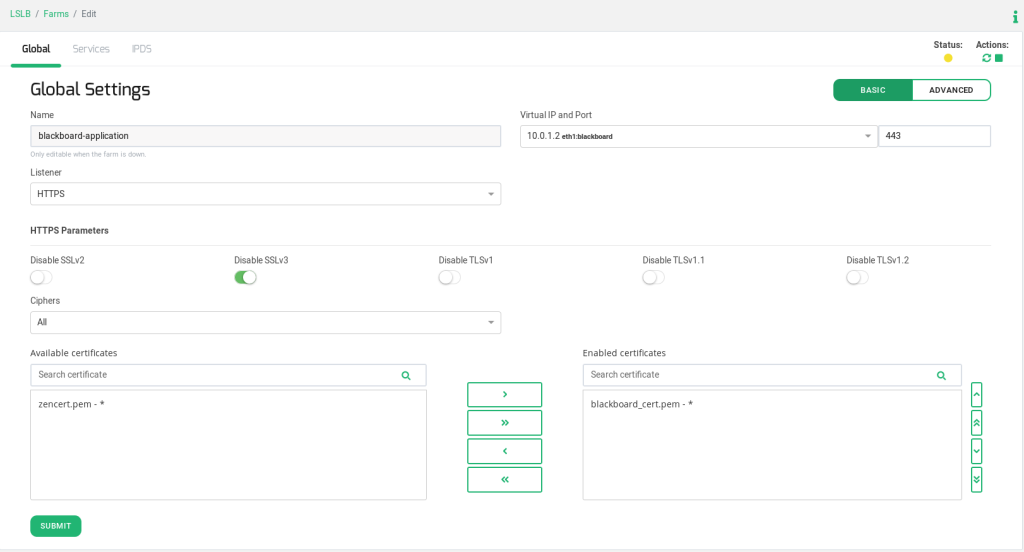
The following parameters will be modified in order to get the best performance:
Listener:
HTTPS
Enabled certificates. Here, it is recommended to choose a signed certificate previously uploaded from left menu bar option LSLB > SSL Certificates, click on the Upload Certificate button.
The Blackboard application only needs one service in the HTTPS virtual service. Create it by clicking on the Services tab and then the New Service button. The parameters to configure in the services are:
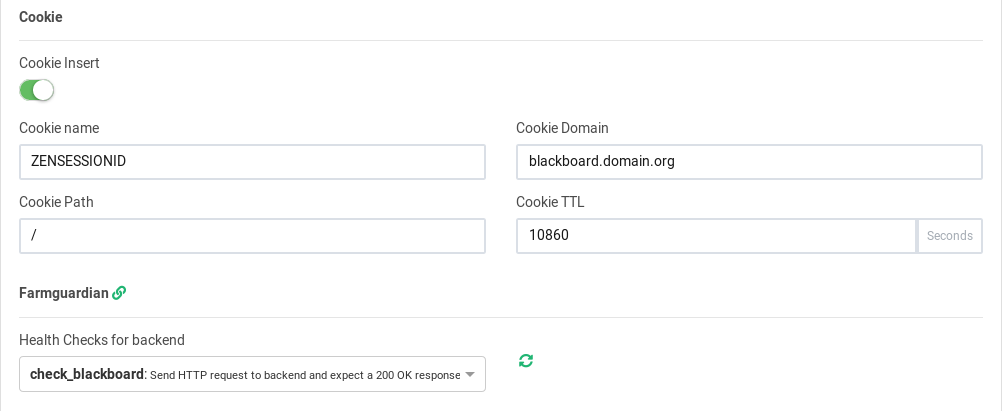
HTTPS Backends: enabled
Cookie Insert: enabled
Cookie name: ZENSESSIONID
Cookie TTL: 10860, (3h, 1min)
Cookie Path: /
Farmguardian: check_blackboard (previously created)
Once modified, it is necessary to press the Submit button.
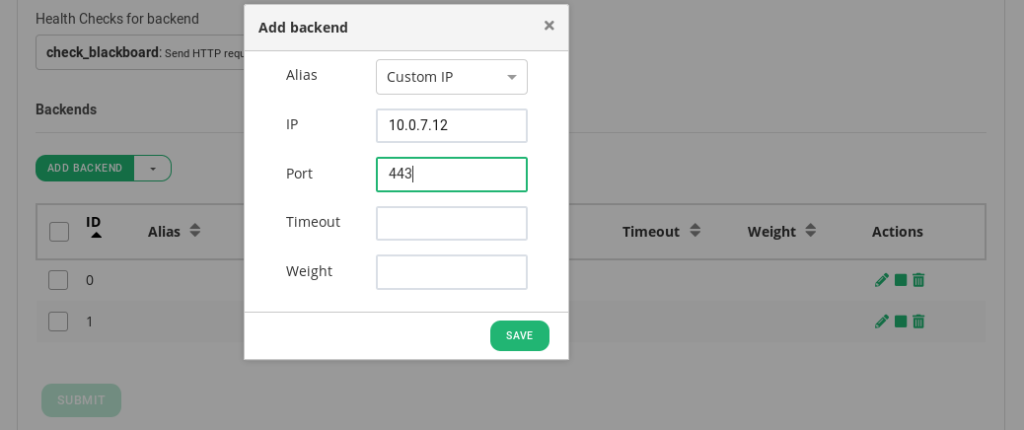
Finally, add the application servers in the backend section by clicking on Add Backends. For each backend is needed to configure the IP Address and the Port. When all backends are added then press the farm Restart button.
Application Server HTTP to HTTPS redirect service
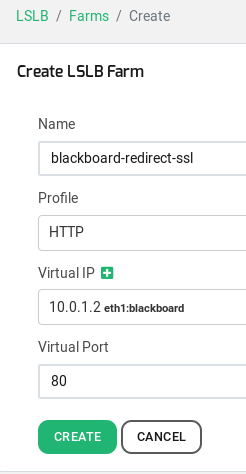
The goal of this HTTP farm is to redirect the HTTP requests to the HTTP farm previously created with the name blackboard-application in order to force all the clients to pass-through the encrypted service. In out example, please create a new LSLB farm called blackboard-redirect-ssl and set the following parameters for this farm:
Name: blackboard-redirect-ssl
Profile: HTTP
Virtual IP: 10.0.1.2 (it is the same than the service in the port 443)
Virtual Port: 80
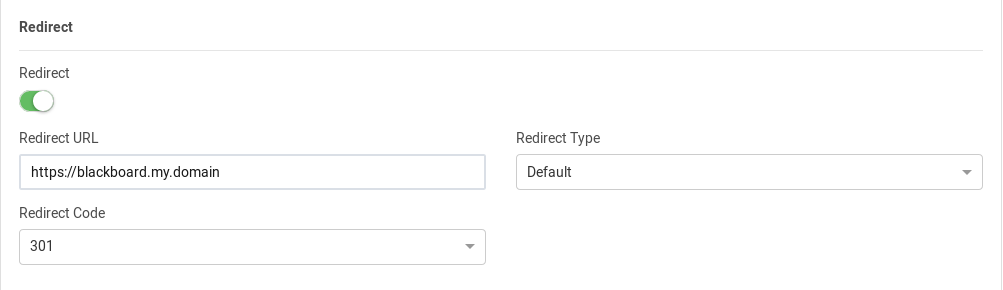
Once the farm has been created, click on the tab Services and the button New Service. Select a service name, redirect in this example, and edit it with the following parameters:
Redirect: enabled
Redirect URL: https://blackboard.domain.org (this is the service nameserver name used in the DNS)
Redirect Type: Default
Redirect Code: 301
Finally, press on Submit and restart the farm in order to apply the changes.
Blackboard Collaborative Servers virtual service configuration
As explained at the beginning of the article, collaborative servers cannot be load balanced according to Blackboard but they can be setup in high availability.
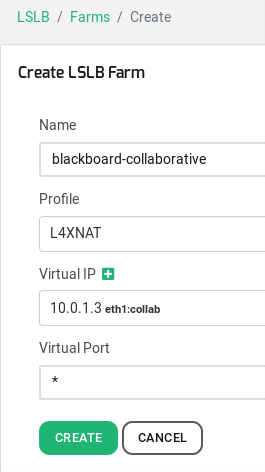
The first step is to set the virtual service by creating a new farm L4xNAT through the section LSLB > Farms > Create Farm. It’s recommended to configure this virtual service with all ports, set by *, and through ALL protocols as Blackboard recommends to enable TCP for the services and some UDP ports in order to improve the performance of the interactive traffic.
No special algorithm or persistence is required, as this service will be configured in active-passive mode, but we’ll add the backends IP addresses (without Port) with different Priority in order to generate the automatic failover when the active collaboration server is detected as down. More than 2 backends could be configured without any problem.
Finally, it’s recommended to configure a health check for this service. As no specific port is used in the virtual service and backends, we’ll use a simple check_ping in order to know if the collaboration server is reachable and responds correctly to an ICMP packet.
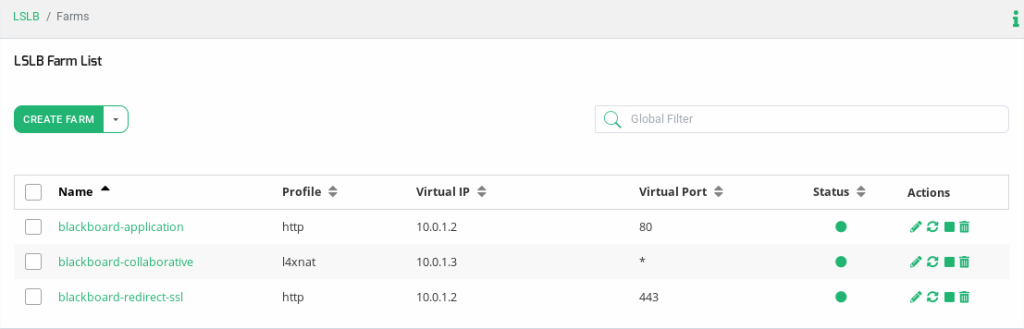
Blackboard virtual services summary
Here you have the summary of the virtual service we’ve created to enhance the Blackboard availability.
Blackboard Load Balancer Cluster
In order to avoid a unique single point of failure, a load balancer cluster is required. This practice allows to setup the whole environment in different data centers or physical nodes.
To get further information about the cluster please refer to https://www.skudonet.com/knowledge-base/howtos/configure-Skudonet-cluster/
Blackboard Virtual Services Enhanced Security
Zevenet Load Balancer includes an Intrusion Prevention and Detection System that includes Blacklists, DDoS protection, DNS realtime blackhole lists, and Web Application firewall. We recommend taking advantage of those security systems for your Blackboard HA implementation.