Modern application delivery architectures are built with the right goals in mind. Load balancers distribute traffic, Web Application Firewalls enforce security policies, TLS protects data in transit, and monitoring systems promise observability across the stack. On paper, everything seems covered.
In real production environments, however, many of these architectures operate with critical blind spots. Especially when security components start making decisions that engineers cannot fully see, trace, or explain. This is rarely caused by a lack of tools. More often, it is the result of how security is embedded into the delivery path.
As security becomes more deeply integrated into application delivery, visibility does not automatically follow.
When security turns into a black box
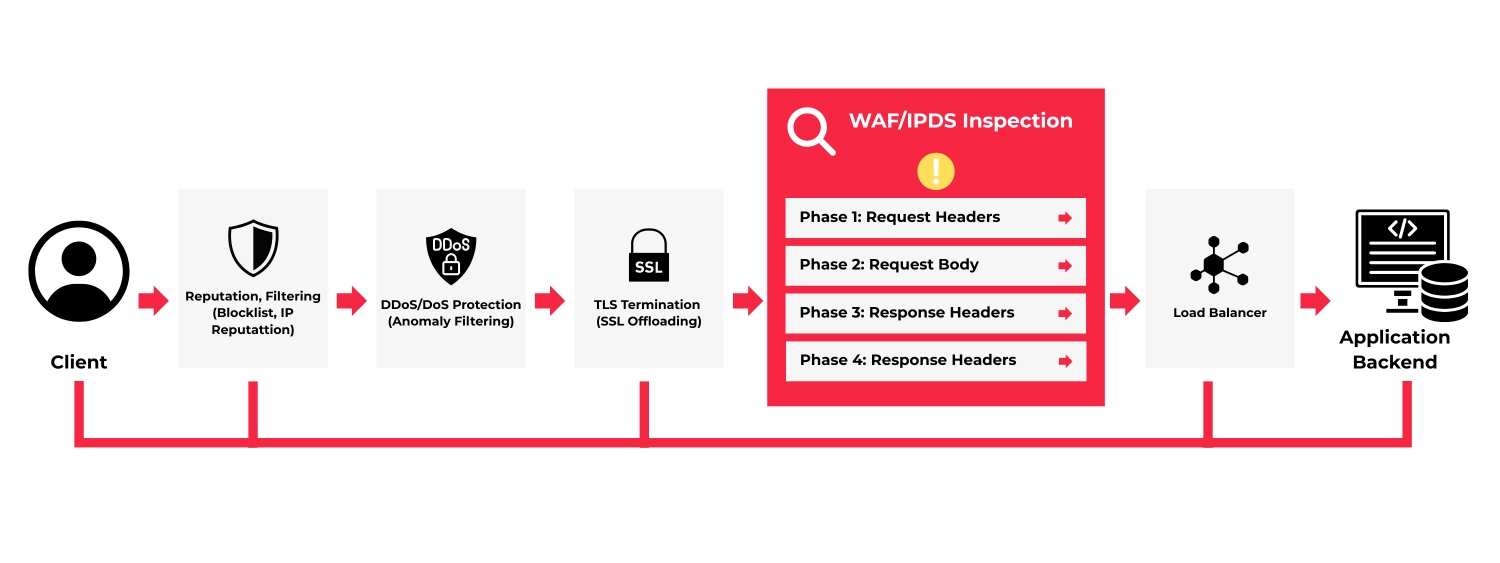
In most production environments, security is no longer a separate layer. WAFs sit directly in the traffic path, inspecting requests, evaluating rules, applying reputation checks and deciding — in real time — whether traffic is allowed or blocked. TLS inspection happens inline, and policies are often updated automatically.
The problem is not that these decisions exist. The problem is that, very often, they cannot be clearly explained after the fact.
In many deployments, teams quickly run into the same limitations:
- Engineers cannot determine which specific rule caused a request to be blocked
- WAF logic is exposed only through high-level categories or abstract scores
- Encrypted traffic is inspected, but the inspection process itself remains invisible
- Logs are available, but without enough context to correlate decisions with behaviour
The result is a paradox that experienced teams recognize immediately: security coverage increases, while operational visibility decreases.
Common Security Blind Spots in Application Delivery Architectures
These blind spots rarely appear during normal operation. They tend to surface under pressure: traffic spikes, false positives, performance degradation or partial outages. When they do, troubleshooting becomes significantly more complex, because the information engineers need is often incomplete or fragmented.
1. Encrypted traffic without explainability
TLS encryption is essential, but it fundamentally changes how visibility works. In many application delivery stacks, traffic is decrypted at some point, inspected, and then re-encrypted. Security decisions are made, but the path between request, rule and outcome is not always traceable.
When something breaks, engineers are often left with little more than a generic message: “Request blocked by WAF.”
What is missing is the ability to correlate:
- the original request,
- the specific rule or condition involved,
- the security decision that was applied,
- and the downstream impact on the application.
Without that correlation, root cause analysis turns into guesswork rather than engineering.
2. Abstracted or hidden WAF rule logic
Many WAF platforms expose protection logic through simplified models such as risk scores, rule categories or predefined profiles. While these abstractions make dashboards easier to read, they remove critical detail from day-to-day operations.
When rule logic cannot be inspected directly:
- false positives are harder to tune with precision,
- rule conflicts remain invisible,
- behaviour changes appear without an obvious trigger.
Over time, this erodes trust in automated protection. Teams stop understanding why something happens and start compensating by weakening policies instead of fixing the underlying issue.
3. Security decisions that impact delivery
Security controls do more than allow or block requests. They influence how connections are handled, how retries behave, how sessions persist, and how backend health is perceived by the delivery layer.
When these effects are not visible, delivery problems are often misdiagnosed:
- backend instability may actually be selective blocking,
- uneven load distribution may come from upstream filtering,
- timeouts may be caused by inspection delays under load.
Engineers end up debugging load balancing logic or application behaviour, while the real cause sits silently inside the security layer.
4. Logs without operational context
Logs are often treated as a substitute for visibility. In practice, they are frequently:
- sampled or rate-limited,
- delayed,
- detached from real-time behaviour,
- owned or processed externally.
A log entry that explains what happened, but not why, is not observability, it is a post-mortem artifact. In critical environments, teams need actionable insight while an incident is unfolding, not hours later.
What Modern WAF Architectures Must Provide
A WAF integrated into the application delivery path should not act as an opaque enforcement layer. Instead, it should provide visibility at each critical stage of the decision process.
In practical terms, this means enabling teams to:Trace each security decision end to end, from the incoming request to the final action applied.
- Trace each security decision end to end, from the incoming request to the final action applied.
- Inspect WAF rule logic directly, without relying on abstract categories or risk scores.
- Correlate blocked or modified requests with delivery behaviour, such as backend health, session persistence or retries.
- Analyze encrypted traffic transparently, without losing context once TLS inspection is performed.
- Maintain consistent visibility under load, during traffic peaks or active incidents.
Without these capabilities, security controls may protect applications, but they also introduce operational blind spots that slow down troubleshooting and increase risk.
Visibility in Secure Application Delivery with SKUDONET
SKUDONET Enterprise Edition is designed around a simple principle: security must protect traffic without breaking visibility.
Instead of treating security as a separate black box, SKUDONET integrates WAF and traffic management into a single, observable application delivery platform. This approach ensures that security decisions remain transparent, traceable and actionable for engineers working in real production conditions.
Key aspects of this design include:
- Full visibility and control over WAF rules and behaviour, allowing administrators to inspect rule logic, modify or disable existing rules, and define new ones based on real traffic patterns and application requirements.
- Clear correlation between security decisions and application delivery impact, making it possible to understand exactly where a request failed, why it was blocked or modified, and how that decision affected backend behaviour.
- Transparent inspection of encrypted traffic, preserving full request context throughout the entire lifecycle, from decryption to enforcement and delivery.
- Actionable logging and diagnostics, designed to explain not only what happened, but why it happened, enabling effective tuning, troubleshooting and auditing.
By removing opacity from security enforcement, SKUDONET helps teams retain control over both protection and performance—especially in high-traffic or business-critical environments where visibility is essential.
A 30-day, fully functional evaluation of SKUDONET Enterprise Edition is available for teams who want to validate this level of visibility and control under real workloads.