Load Balancers are a key device in our infrastructure as they are used to distribute traffic across different networks, they are the entry point of applications and even of a whole data center. For that reason, cybersecurity and the security access of different users to the device is an important matter to address.
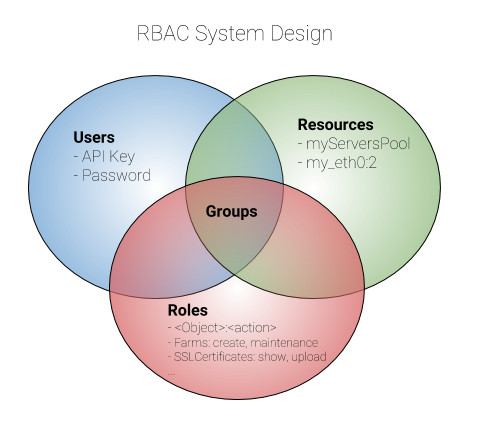
The main goal of implementing a Role Based Access Control (RBAC) system is to provide to any organization a flexible tool to manage their users, roles and resources defined in the load balancer, such as virtual services or virtual network interfaces. Given that ability, different roles in an organization like network administrators, system administrators, devops, developers or operators, can control their own resources allowing a more agile work group and isolating different projects and scopes.
How the RBAC system has been designed?
SKUDONET Dev Team has designed the RBAC system in a standard and easy to maintain infrastructure, but compatible with all the different modules included in SKUDONET.
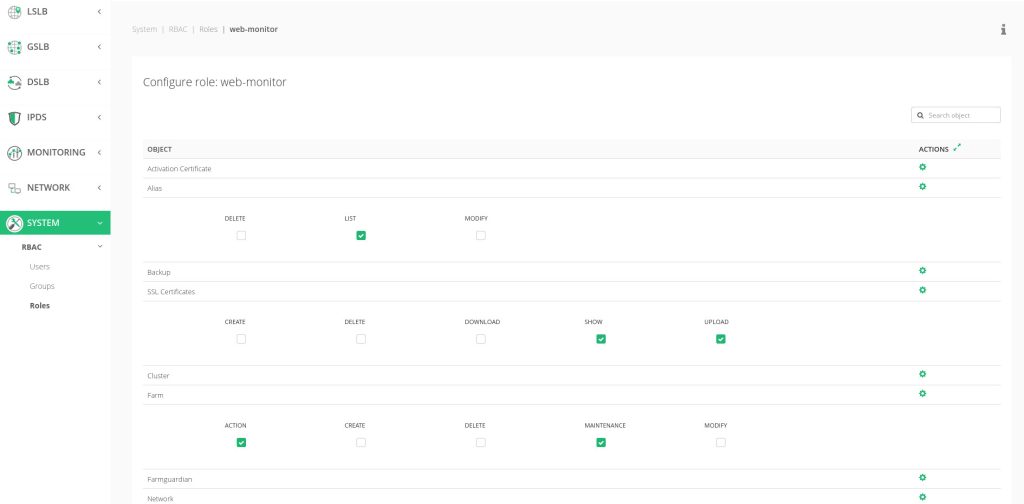
There are new concepts in the new infrastructure like Users, which are provided with a password and independent Zapi Key per user which allows the remote access through API and even control the access through the web GUI. Roles are a compound of predefined objects with their specific actions that can be enabled or disabled according to the role to be created. Resources are the different instances created in the load balancer like a certain farm servers or virtual interfaces. Groups are defined as the association of Users, Roles and Resources. A descriptive diagram is shown below.
Users password are fully encrypted with the highest level of security and synchronized with the system, although they’re not going to have access to the load balancer through command line.
There are predefined roles templates for the different profiles in any organization so the RBAC system has been designed to be easy to adopt and maintain.
How are the security processes integrated with the new RBAC system?
The data security has been taken into consideration in order to protect the sections where the load balancer gathers most sensible data like the listing of network interfaces or aliases which provides information about the topology of the network, read and download of logs files where all the information of the load balancer is centralized, upload or download backups with the full configuration of the load balancer or even the section of support data to help our support team to analyze any issue in the load balancer.
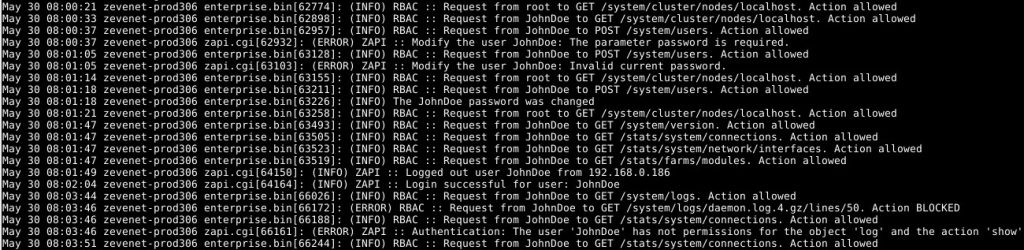
In addition, an the new RBAC provides an Audit system where all the interactions from users accessing to the load balancer or applying any of their actions are logged, so any change in the load balancer can be audited and controlled by the security team, successful or forbidden ones with their corresponding tag.
Next challenges in terms of RBAC would be: physical resources limitation per user using cgroups (like CPU, throughput, memory, etc), further operating system hardening or the support of multiple groups per user.
As the RBAC system is designed to be fully scalable, new great abilities are coming.
Look forward to the SKUDONET EE 5.2 release!