Contents
In today’s digital landscape, network security and efficient data management are not merely buzzwords but essential pillars of any organization’s success. Among the various tools and techniques employed to achieve these goals, Virtual Local Area Networks (VLANs) stand out as a powerful solution that can significantly contribute to enhancing network security, optimizing performance, and streamlining data management.
What are VLANs and How Do They Work?
In essence, VLANs are a method of logically segmenting a single physical network into multiple virtual networks. This segmentation is achieved by assigning a unique VLAN identifier (VLAN ID) to each virtual network. Devices that are assigned to the same VLAN ID can communicate with each other as if they were on a dedicated physical network. However, devices on different VLANs cannot communicate with each other directly. This is because VLANs act as separate broadcast domains, meaning that broadcasts are not forwarded between VLANs.
To enable communication between devices on different VLANs, a router or Layer 3 switch must be used. The router or Layer 3 switch acts as a gateway between the VLANs, routing traffic between them as needed.
Real-World Examples of VLAN Implementation
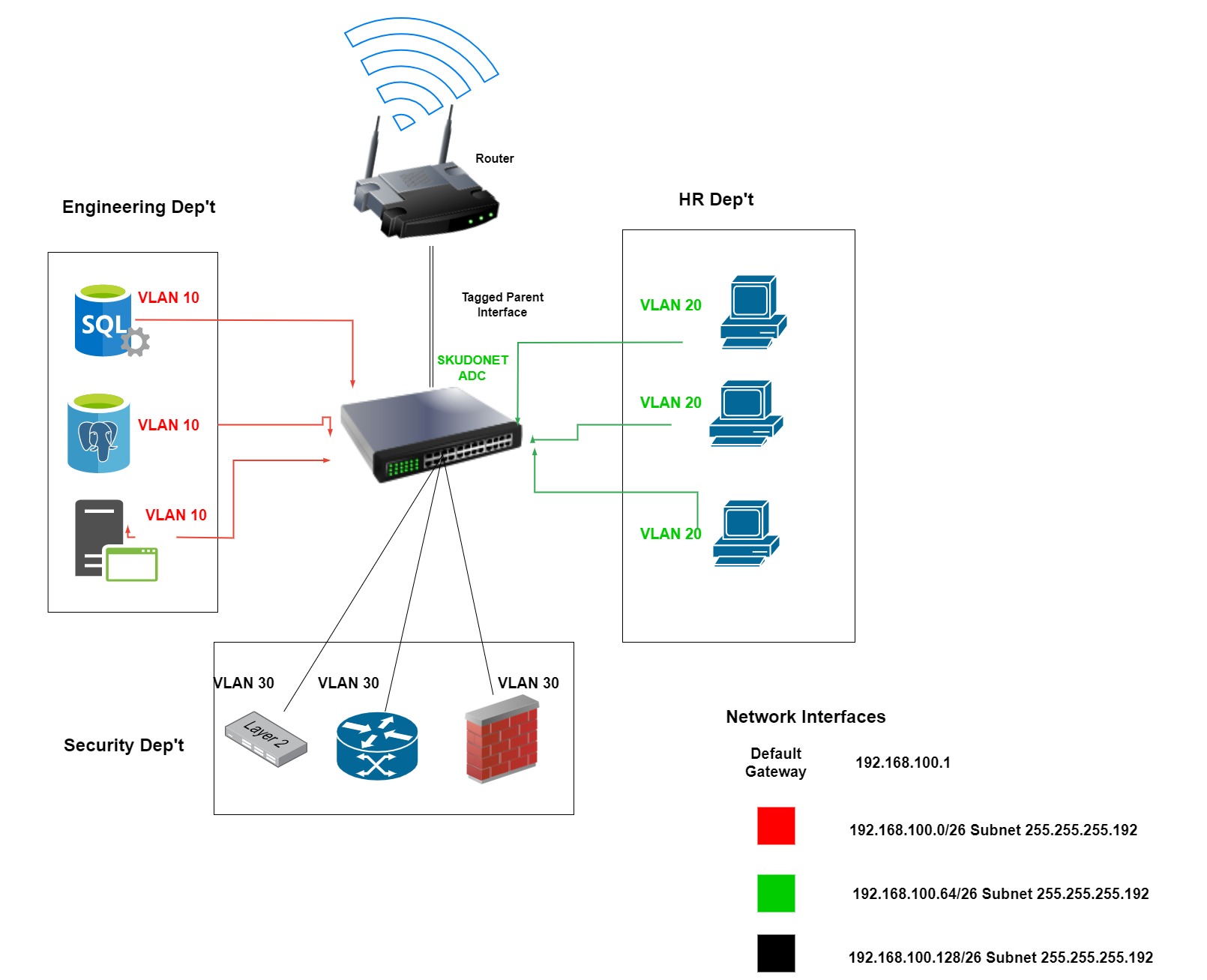
Let’s consider a scenario where an organization has three distinct departments: Security, Engineering, and HR. Each department has its own unique data security and access requirements. By implementing VLANs, the organization can logically segment the network into three separate VLANs, one for each department.
- Engineering VLAN: The Engineering VLAN would be assigned VLAN ID 10 and would be used to house all engineering workstations and servers.
- HR VLAN: The HR VLAN would be assigned VLAN ID 20 and would be used to house all HR workstations and servers.
- Security VLAN: The Security VLAN would be assigned VLAN ID 30 and would be used to house all security-critical devices, such as firewalls, intrusion detection/prevention systems (IDS/IPS), and security information and event management (SIEM) systems.
By segmenting the network into separate VLANs, the organization can ensure that sensitive data is only accessible to authorized personnel. For example, employees in the HR department would not be able to access data on the Security VLAN, and employees in the Engineering department would not be able to access data on the HR VLAN.
Important Notice!
By default, interfaces on a SKUDONET ADC do not have a VLAN tag associated with them. This means that a broadcast frame sent by one device will be received by all devices on the same network. This can create security vulnerabilities, as it allows unauthorized devices to access sensitive information. To mitigate this risk, it is important to create different VLANs for different departments. This will isolate traffic between departments and prevent unauthorized access to sensitive information.
Benefits of VLAN Implementation
The implementation of VLANs offers a multitude of benefits for organizations, including:
- Enhanced network security: By isolating sensitive data on separate VLANs, organizations can significantly reduce the risk of unauthorized access to critical data.
- Improved network performance: By segmenting high-traffic devices from low-traffic devices, organizations can improve overall network performance by reducing congestion.
- Efficient data management: By grouping devices based on their function or department, organizations can simplify data management and make it easier to comply with data security regulations.
- Increased flexibility: VLANs provide organizations with the flexibility to quickly and easily add new devices or services to the network without having to make major changes to the physical network infrastructure.
VLAN Interfaces List
This table shows all the VLAN interfaces that are configured in SKUDONET ADC.
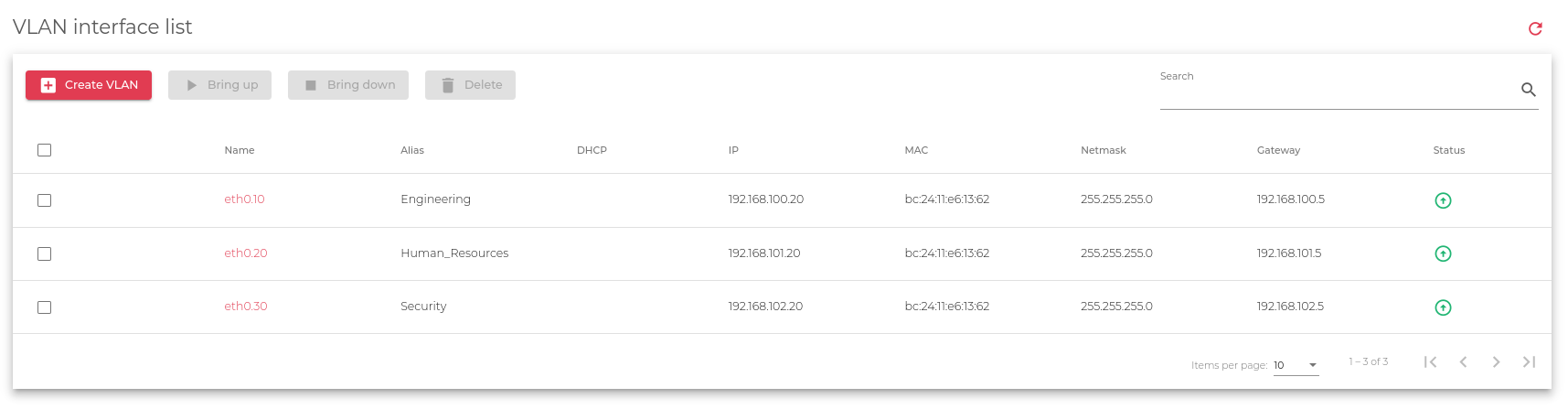
The table above shows the VLAN interfaces on the system and their configuration information.
Name: A unique identifier for the VLAN interface.
IP: The IP address of the VLAN interface. Supports both IPv4 and IPv6.
Alias: A descriptive name for the VLAN configured.
MAC: The MAC address of the VLAN interface. The VLAN inherits the MAC address from the parent NIC.
Netmask: The subnet mask of the VLAN interface. Can only be configured if the IP address is also configured.
Gateway: The default gateway used by the VLAN interface. Must be on the same subnet as the VLAN interface.
Status: The status of the VLAN interface.
 Green: The VLAN interface is up and running.
Green: The VLAN interface is up and running. Red: The VLAN interface is down.
Red: The VLAN interface is down.
Perform the following Actions in the VLAN section:
- Create VLAN: Create a new VLAN interface.
- Bring Up: Start the interface and allow it to receive and transmit traffic.
- Bring Down: Stop the interface from receiving and transmitting traffic.
- Delete: Remove the VLAN interface.
- Edit: Change the VLAN configurations, such as the IP address, MAC address, netmask, and gateway.
Next Article: Network | VLAN | Create