Contents
Overview
Barracuda Networks offers a range of Network security and Application delivery products, and an ADC is part of their product line. Though these products address the needs of many consumers, various resources point out some potential downsides, and these downsides include;
- Some users find the initial setup configurations difficult, which can be time-consuming and require a higher level of technical expertise.
- Both technical and customer support can be slow, and one may struggle to find resources.
- The performance of some of the Barracuda products, such as the firewall appliances, can be impacted when handling large amounts of traffic.
It is imperative to evaluate whether the features and functionalities of the Barracuda products align with your specific needs. This guide will help gracefully transition your ADC services from Barracuda Networks to SKUDONET if you need a service shift.
Prerequisites
To effectively follow this guide, ensure you meet the following prerequisites.
- You must’ve installed an instance of SKUDONET ADC on your PC, bare-metal, or virtual environment, or you must have an active ZVNcloud account. For on-premise deployment, Request an evaluation.
- You must have access to the Web User interface. If you don’t, follow this quick Installation guide.
- You must be an active user of the Barracuda Networks and be familiar with the concepts we will discuss in the section below.
- Ensure that you create a virtual server in the SKUDONET load balancer. Here is a quick guide: Layer 4 and Layer 7 Virtual Server Configuration
Basic Concepts
High Availability: This mechanism is responsible for maintaining the uptime of web services even when some servers abruptly go down or are in maintenance mode. One obtains HA by configuring A Master/Backup pair. To access HA configurations on SKUDONET, Access System >> Cluster.
GLSB Services: Global Load balancing provides clients access to resources from data centers closest to their regions, improving the speed of delivery. GSLB can also be used for disaster recovery if one data center fails. This type of load balancing occurs at the DNS level. SKUDONET offers DNS load balancing through the GSLB >> Farms.
Server monitor: These are health checks that monitor whether a backend server or its service is up or down. SKUDONET implements health checks through Farmguardian.
Access and Audit logs: These log files help admins keep track of all activity within the ADC. This activity could be log-in details, network logs, system errors, etc. One may view system logs on SKUDONET by accessing System >> Logs.
DDoS Prevention: This security feature protects many forms of DoS attacks. These could be Bogus TCP flags, HTTP flood attacks, Ping flood attacks, etc. One may use DoS prevention and protection in SKUDONET by accessing IPDS >> DOS.
Security: This feature monitors and controls all traffic flowing through an ADC. It ensures that all the traffic is legitimate while filtering out all illegitimate traffic. SKUDONET implements security through the IPDS module.
Allow/Deny Rules: An admin uses these rules to limit traffic from accessing particular resources. One may configure them to block external traffic and whitelist internal IPs to use admin privileges within an organization’s network. An admin may configure the rules to block traffic from certain geolocations. SKUDONET implements Allow/Deny Rules through IPDS >> Blacklists.
Servers: These are physical servers or VPS placed within an ADC service. They are responsible for processing all client requests. With SKUDONET ADC, we call servers Backends.
Services: A service in Barracuda is responsible for receiving all incoming traffic and forwarding it to backends. Services also include a Virtual IP Address and Virtual Port. A similar functionality in SKUDONET is a Farm.
Certificates: These are Self-signed or CA-signed SSL/TLS certificates used for encrypting and decrypting traffic on the ADC, with the purpose of SSL offloading. Within SKUDONET, one may import a custom certificate or configure one with the inbuilt Let’s Encrypt program. Access SSL Certs on SKUDONET ADC through LSLB >> SSL Certificates.
Example configurations: Session persistence
Session persistence refers to the ability of a load balancer or other network infrastructure to ensure that a particular user’s requests are sent to the same backend server in a cluster rather than being distributed randomly. This is useful when the backend server needs to maintain state information about a user, such as the contents of a shopping cart or the progress of a multi-step form. There are several methods for achieving session persistence; These include IP hash, cookie-based persistence, SSL session ID persistence, etc.
In this section, we will make barracuda configurations for Session persistence and use them to describe SKUDONET configurations.
Barracuda Configurations
To Enable session persistence, ensure you have already configured backend servers to serve traffic within the Barracuda services.
Instructions:
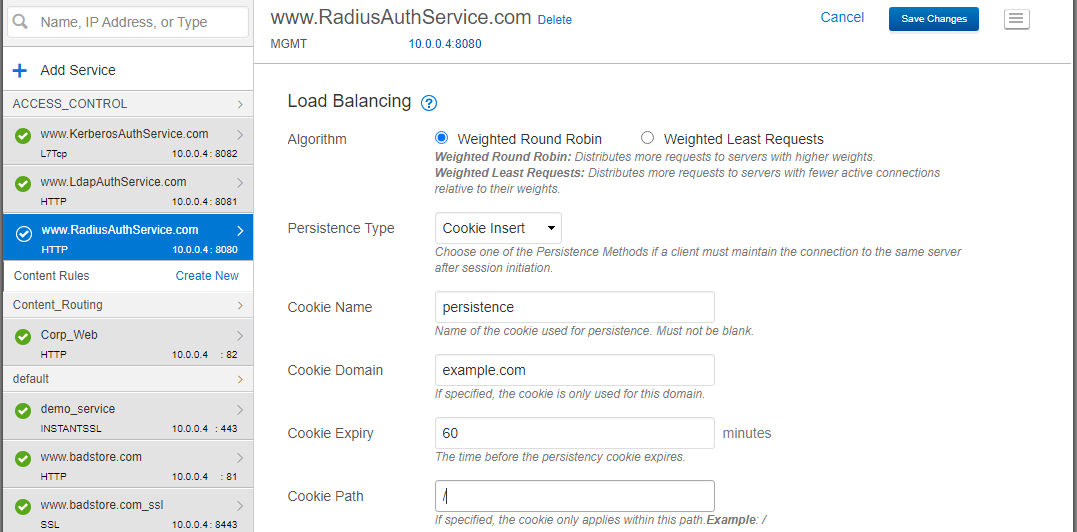
- Click BASIC >> Services.
- Click on the Service you want to enable cookie persistence from the left sidebar.
- Scroll to the section, Load Balancing.
- Click on the drop-down menu of Persistence Type; you will find various types like source IP, cookie Insert, cookie Passive, HTTP Header, and URL parameter. For this example, choose cookie insert.
- Enter the cookie Domain.
- Enter the expiry time in minutes.
- Enter the cookie path.
- Click the Save changes button at the top right of the menu bar.
- Test to see whether the load balancing persists to one backend server.
SKUDONET Configurations
Ensure you have configured an HTTP or HTTPS Farm within the LSLB Farm section. If you have not created one, follow this guide. Layer 4 and layer 7 virtual servers.
Instructions:
- Click the LSLB >> Farms.
- Click the HTTP or HTTPS Farm you created from the LSLB Farms list.
- Click the Services tab and open the service of interest.
- Scroll to the section with Persistence; you will find options like IP: client address, BASIC: Basic authentication, PARM: An URI Parameter, URL: A request Parameter, and COOKIE: A certain cookie. For this example, we will choose COOKE: A certain cookie.
- Configure the Persistence session time to live in seconds.
- Enter a persistence session identifier.
- Scroll down and click the Apply button.
Example configurations: Content rules(Header Rewrites)
Header rewrites are techniques used in web servers and reverse proxies(load balancers) to modify the headers of an incoming HTTP request or an outgoing HTTP response. Modifying HTTP headers is used for various purposes like adding security headers, redirecting requests, or altering the behavior of the server or application. HTTP request headers that can be rewritten include host, user-agent, and referer and the response headers include location, cache control, and content type. The specific method for implementing header rewrites varies depending on the web server or reverse proxy.
For security purposes, sometimes we must edit the server name or its versions so we don’t give out lots of information to online users. In this section, we will configure header rewrites in SKUDONET based on Barracuda configurations to rewrite the server name within the HTTP response header.
Barracuda Configurations
Instructions:
- Click TRAFFIC >> Web Translations.
- Leave Groups as All and select the Service you want the rule to apply.
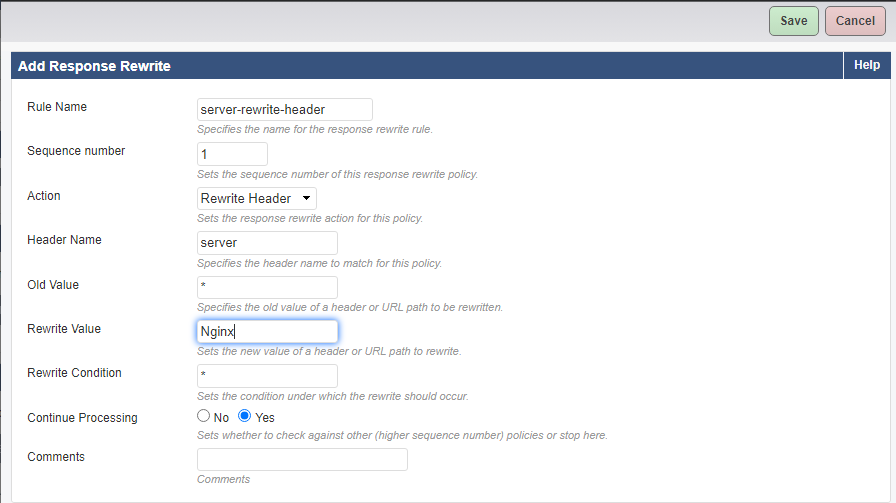
- Within the HTTP Response Rewrite section, click the Add rule button.
- Enter the Rule Name.
- Enter a Sequence Number.
- Within the Action field, select Rewrite Header.
- Enter the Header Name, for example, server.
- For Old Values, you may enter an asterisk(*).
- Enter the Rewrite Value, for example, Nginx.
- Click the Save button.
SKUDONET Configurations
These are SKUDONET configurations based on the previous Barracuda configurations.
Instructions:
- Click LSLB >> Farms.
- Click on the HTTP Farm you want to enable the rule within the HTTP Farms list.
- Click on the Advanced Toggle button within the Global Settings.
- Within the Advanced Settings section, click on the first option, Rewrite location headers, and change the value to Enabled.
- Scroll to the Headers section.
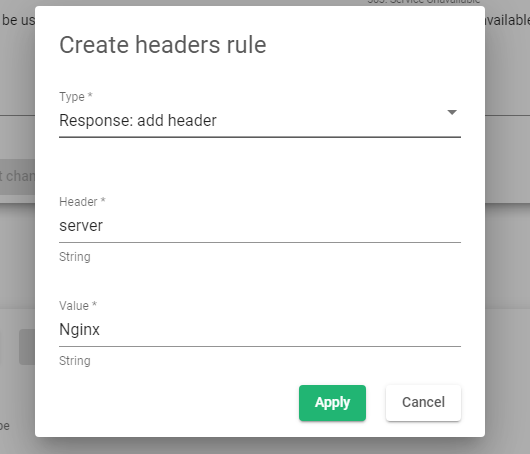
- Click the Create rule button.
- Within the Type* field, select Response: add header.
- Within the Header* field, enter the Header you would like to apply the rewrite rules, e.g., server.
- Within the Value* field, enter the expected value, e.g., Apache.
- Click the Apply button to save the configurations.
- Restart the Farm for the rule to apply
Additional Resources
Web Application Firewall configuration.
Configuring SSL certificates for the load balancer.
Using the Let’s encrypt program to autogenerate an SSL certificate.
Application, Health and Network Monitoring in SKUDONET ADC.
Datalink/Uplink load balancing With SKUDONET ADC.
DNS load balancing with SKUDONET ADC.