Contents
Overview
When designing and building highly available and mass-scalable applications, a reliable system like SKUDONET ADC is an absolute necessity. With the rising demand for real-time delivery, Fast writes and reads to databases, brands must adapt the to the latest specs and protocols so as to stay relevant within the marketplace. Security is a crucial element to the safety of customer data, and this element gives SKUDONET a huge edge over Haproxy.
As a current haproxy user, we will discuss concepts that you’re already familiar with and use them to make similar configurations using SKUDONET ADC.
Prerequisites
One must meet these basic requirements to transfer configurations from Haproxy to SKUDONET ADC.
- An instance of ZEVENET ADC must be installed on your PC, bare-metal, virtual environment, or one must have an active ZVNcloud account. Request an evaluation for on-premise deployment.
- One must have access to the Web graphical interface. If you don’t, follow this quick Installation guide.
- We assume you are an active user of Haproxy and you are familiar with the concepts we will discuss in the section below.
- One must be able to create a virtual server in the SKUDONET load balancer. Here is a quick guide: Layer 4 and Layer 7 Virtual Server Configuration
Basic Concepts
In this section, let us discuss a few concepts based on the HAproxy configuration. We will outline similar ideas in SKUDONET ADC and later use them to describe SSL offloading and HTTP to HTTPS redirection using SKUDONET load balancer.
mode: The mode command defines whether the load balance profile is layer 4 or layer 7. SKUDONET uses Profiles for defining whether the configuration is Layer 4 or 7. These profiles include HTTP and L4xNAT
timeout connect: Timeout connect defines how long HAproxy should wait before connecting to a backend server. SKUDONET uses backend connection timeout. The default value is 20 seconds.
timeout client: This setting defines how long HAproxy should wait for a response from the client. If this time expires without receiving a signal from the client, the connection will terminate. SKUDONET uses client request timeout. The default value is 30 seconds.
timeout server: Timeout server defines how long HAproxy should wait for a response from a backend server. If this time elapses without a response from a backend server, the connection will terminate. SKUDONET uses backend response timeout. The default value is 45 seconds.
bind: Bind defines one or multiple listening IP addresses bundled with their ports. This port(s) listen(s) for incoming traffic and then server them to the backend servers. Here is a sample expression:
listen http_https_proxy_www.
bind ipv6@:80
bind ipv4@public_ssl:443 ssl crt /etc/haproxy/site.pem
The Front Facing section of SKUDONET ADC is a Farm and it has listeners that distribute traffic to various Services.
maxconn: Limits the number of connections HAproxy will serve. This command protects the load balancer from running out of memory. SKUDONET ADC is highly optimized to server over 140,000 concurrent connections at layer 7 and over 10 million connections at layer 4. However, you can establish the maximum number of connections within an L4xNAT profile using the Max. Conns field when configuring Backends.
ssl-default-bind-ciphers: Bind ciphers define the default TLS/SSL ciphers on HAproxy. SKUDONET load balancer comes with preloaded high security ciphers, SSL offloading, and the end-user can customize their ciphers through the custom security flag.
ssl-default-bind-options: This feature disables or enables older versions of TLS/SSL. Access a similar configurations through HTTPS parameters within the Global settings of an HTTP profile on SKUDONET ADC.
Example configuration: SSL offloading and Use of Ciphers
SSL Offloading refers to decrypting incoming SSL/TLS traffic and forwarding it to one or more servers in unencrypted form. The load balancer/Reverse-proxy uses a suite of algorithms (Ciphers) to encrypt and decrypt data.
The use of ciphers in SSL/TLS termination is important because it determines the level of security that is provided for the transmitted data. In general, stronger ciphers provide more secure communication, but they may also require more processing power to encrypt and decrypt the data. As a result, it is important to carefully consider which ciphers are used in SSL/TLS termination, taking into account both security and performance.
HAproxy configurations
To set up ssl offloading with HAproxy, we use the settings below.
frontend myDomain
mode http
bind :80
bind :443 ssl crt /etc/ssl/certs/Skudonet.com.ssl.pem
default_backend domainBackends
From the snippet above, Haproxys listen for incoming traffic on both ports, 80 and 443. However the port 443 includes a directive to directory where the ssl certificate is saved.
Meanwhile, you can specify the default ciphers to use on the load balancer by the settings: ssl-default-bind-ciphers and the ssl version using ssl-default-bind-option.
ssl-default-bind-ciphers ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256
ssl-default-bind-options ssl-min-ver TLSv1.2 no-tls-tickets
SKUDONET configurations
To achieve a similar result with SKUDONET, ensure you have created an HTTP farm profile. If you forgot, refer to this article: Layer 4 and Layer 7 Virtual Server Configuration
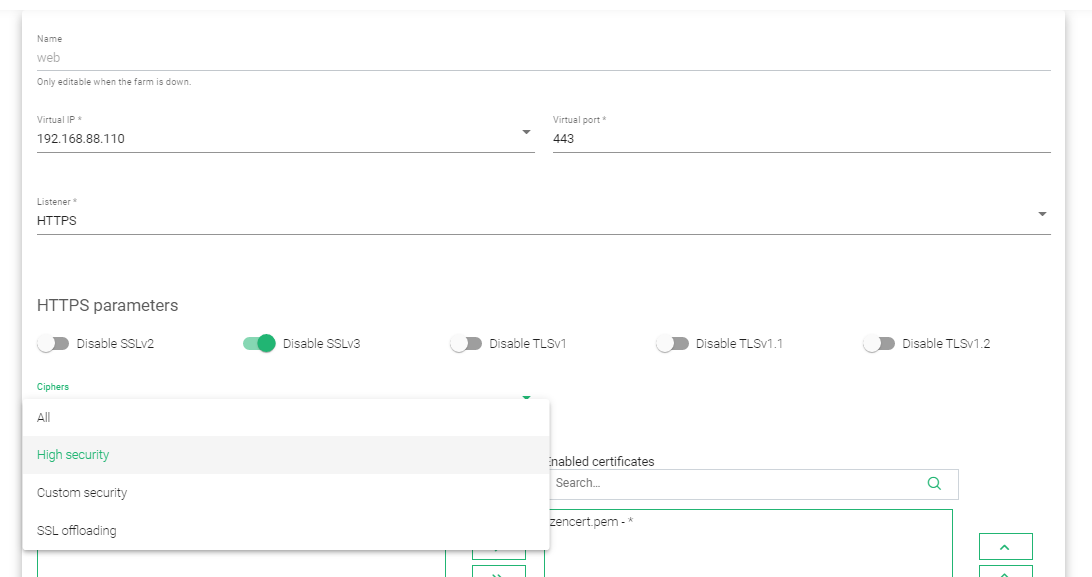
- On the Menu, go to LSLB > Farms and click on the layer 7 (HTTPS) farm profile.
- Under general settings, change the port number to 443.
- Change the Listener from HTTP to HTTPS.
- Under HTTPS parameters, enable or disable old TLS/SSL versions.
- Choose SSL offloading as your cipher.
- The load balancer is preload with a zencert.pem SSL certificate, but you can include a custom certificate if you have created one.
- Update the configurations by clicking the Apply button.
To learn more about the HTTP profile, SSL certificates and configuring a custom SSL certificate using the Let’s Encrypt on SKUDONET ADC, refer to these guides.
- Layer 7 (HTTP Profile) in SKUDONET ADC.
- SSL certificates on SKUDONET ADC.
- Let’s Encrypt program on SKUDONET ADC.
Example configurations: HTTP to HTTPS Redirection
When clients visit services through an unsecured port, sometimes you must redirect them to a secure server. We achieve this by responding with a permanent redirection status code 301. The client’s browser will automatically to connect to the secure IP and port sent in the location header.
Haproxy configurations
With haproxy, the code http-request redirect redirects users if they visit through port 80 to port 443.
frontend myDomain
mode http
bind :80
bind :443 ssl crt /etc/ssl/certs/ssl.pem
http-request redirect scheme https unless { ssl_fc }
default_backend domainBackends
HTTP to HTTPS redirection in SKUDONET ADC
Using the Steps outlined in this article: Layer 4 and Layer 7 Virtual Server Configuration, create both an HTTP and an HTTPS Farm.
Ensuring that you have both the HTTP and HTTPS farms;
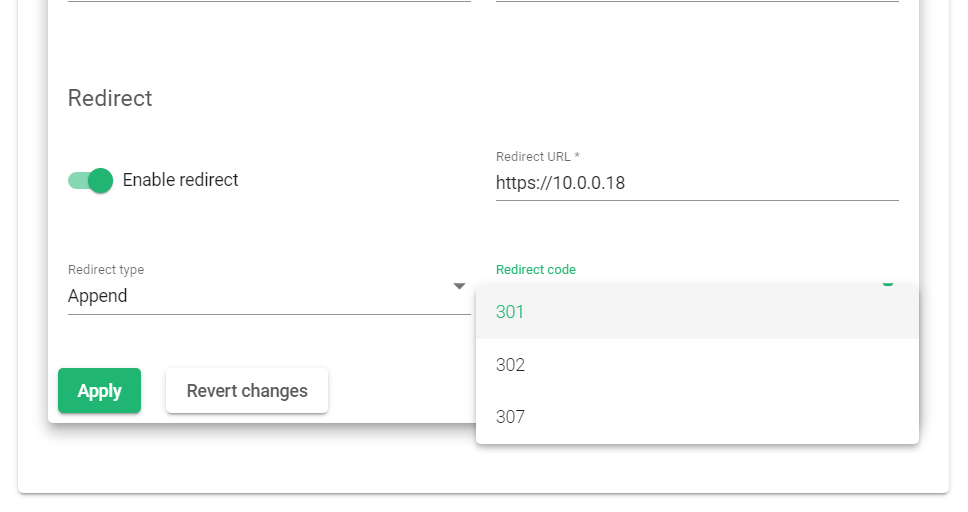
- Go to LSLB > Farms and click the Edit Icon of the HTTP farm.
- Click the Services tab and open the service you want to Edit.
- Toggle on the enable redirect button.
- Choose redirect type Append.
- Select the redirect code: 301.
- Enter the redirect URL by prepending https:// to the IP address. If the IP address of the secure Farm is 10.0.0.18, then the redirect url will be https://10.0.0.18
- Update the changes by clicking the Apply button.
- Restart the farm for changes to take effect.
Also watch:
Additional Resources
Using the Let’s encrypt program to autogenerate an SSL certificate.
Datalink/Uplink load balancing With SKUDONET ADC.
DNS load balancing with SKUDONET ADC.
Protection from DDoS attacks.
Application, Health and Network Monitoring in SKUDONET ADC.
Web Application Firewall configuration.
Configuring SSL certificates for the load balancer.